New in 2.19: Extension Flood Filter
With the release of SmartFoxServer 2.19.0 we have introduced a new Extension Flood Filter that provides fine grained control over the packet rate of Extension requests: it can be used to limit the number of calls per second for specific requests and automatically set rules for warning and banning the offending client(s).
It also includes the ability to catch unknown Extension calls (i.e. requests for which there doesn’t exist a request handler) and apply auto-ban rules as well.
Under normal circumstances, e.g. users playing with the official client app, there shouldn’t be a concern about request spam: limitations can be easily coded in the client itself. However it’s also relatively easy for malicious users to reverse engineer a client made in Javascript, Unity or Java and bypass such limitations.
Overview
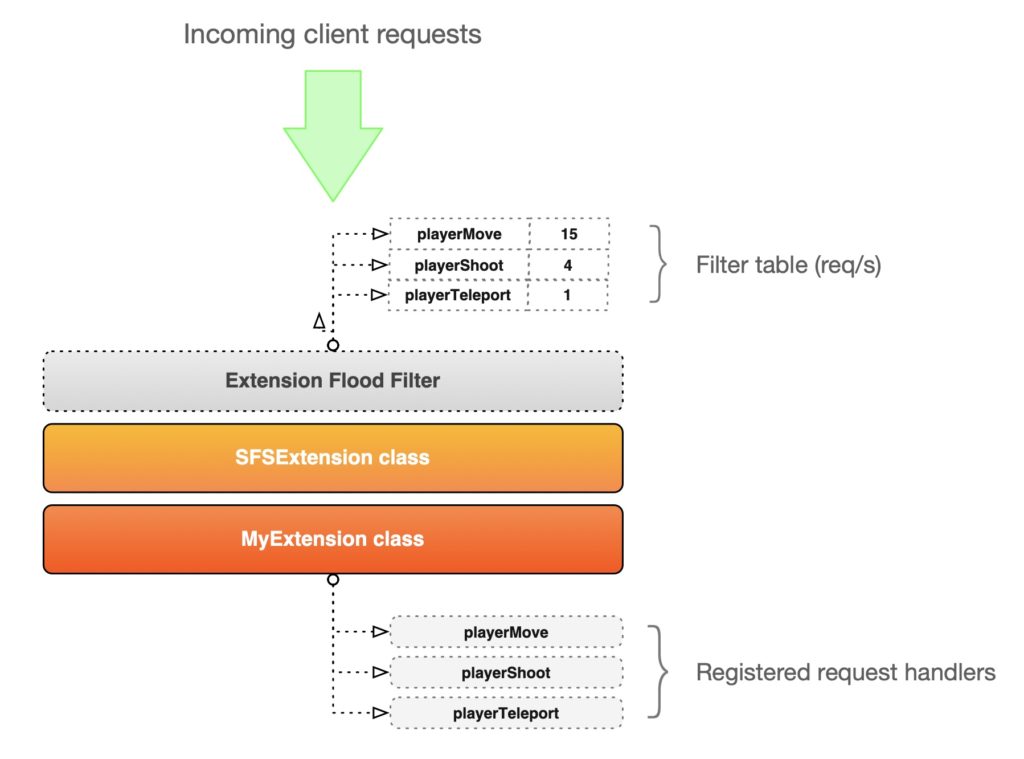
In the diagram below we show a bird’s eye view of the filter and its position in the Extension invocation chain. For each request handler defined in our Extension code (via the addRequestHandler methods) we can set a limit expressed in number of calls per second.
In this example we have defined a playerShoot request handler and we’ve also set a limit of 4 requests/sec. If a client sends 20 calls in one second only the first 4 will be passed to the Extension and processed, while the rest will be discarded. Additionally, based on the auto-ban rules, the sender will either be warned or banned.
Usage
The Extension Flood Filter is inactive by default. To activate it we need to call the initFloodFilter(…) method available from the parent SFSExtension class.
public class AntiFloodTestExtension extends SFSExtension
{
static final String PLAYER_SHOOT = "pShoot";
static final String PLAYER_MOVE = "pMove";
@Override
public void init()
{
ExtensionFloodFilterConfig cfg = new ExtensionFloodFilterConfig();
cfg.banDurationMinutes = 120;
cfg.maxFloodingAttempts = 3;
cfg.secondsBeforeBan = 2;
cfg.banMessage = "You are now banned. Reason: request flooding.";
cfg.filterRules = Map.of
(
PLAYER_SHOOT, 4,
PLAYER_MOVE, 15
);
initFloodFilter(cfg);
addRequestHandler(PLAYER_SHOOT, (sender, param) -> {
trace("Shooting");
});
addRequestHandler(PLAYER_MOVE, (sender, param) -> {
trace("Moving");
});
}
}
The initializer method takes a ExtensionFloodFilterConfig object with with a number of properties for warning and banning clients.
For more details on each setting, default values and further details please check our documentation website here.
